A Certified Ethical Hacker (CEH) degree is a certification that provides specialized skills in identifying vulnerabilities and weaknesses in computer systems and networks. It is increasingly important in today's world where cybersecurity threats are becoming more frequent and complex.
Obtaining a CEH certification enhances the career prospects of cybersecurity professionals, as it validates their expertise and commitment to the field. It can potentially lead to higher-paying job roles and advancement opportunities.
Moreover, a CEH degree is crucial for businesses and organizations that handle sensitive data, as it demonstrates a commitment to secure their networks and protect their assets from cyberattacks. This certification can be a crucial factor in ensuring the trust and confidence of customers, partners, and stakeholders.
In summary, a CEH degree is important because it provides specialized skills to combat cybersecurity threats, enhances career prospects, and instills confidence in businesses and organizations by demonstrating a commitment to cybersecurity.
Date : ( 28 / 11 / 2022)
During my time as a Teaching Assistant at KCST, I had the privilege of delivering a
captivating lecture on Kali Linux, an exceptional operating system specifically tailored
for the domains of penetration testing and digital forensics. Being built upon the solid
foundation of Debian, Kali Linux empowers ethical hackers, security professionals, and
enthusiasts with an extensive array of cutting-edge tools and resources. Equipped with
a rich selection of pre-installed software and utilities, this robust platform enables
vulnerability assessments, network scanning, password cracking, and much more. Through my
engaging presentation, I introduced attendees to the exhilarating realm of ethical hacking,
enlightening them on how to harness the power of Kali Linux to enhance their cybersecurity
prowess. It was a rewarding experience to witness their enthusiasm as they embarked on their
journey to bolster their skills in the ever-evolving field of cybersecurity.
Date : ( 21 / 11 / 2021)

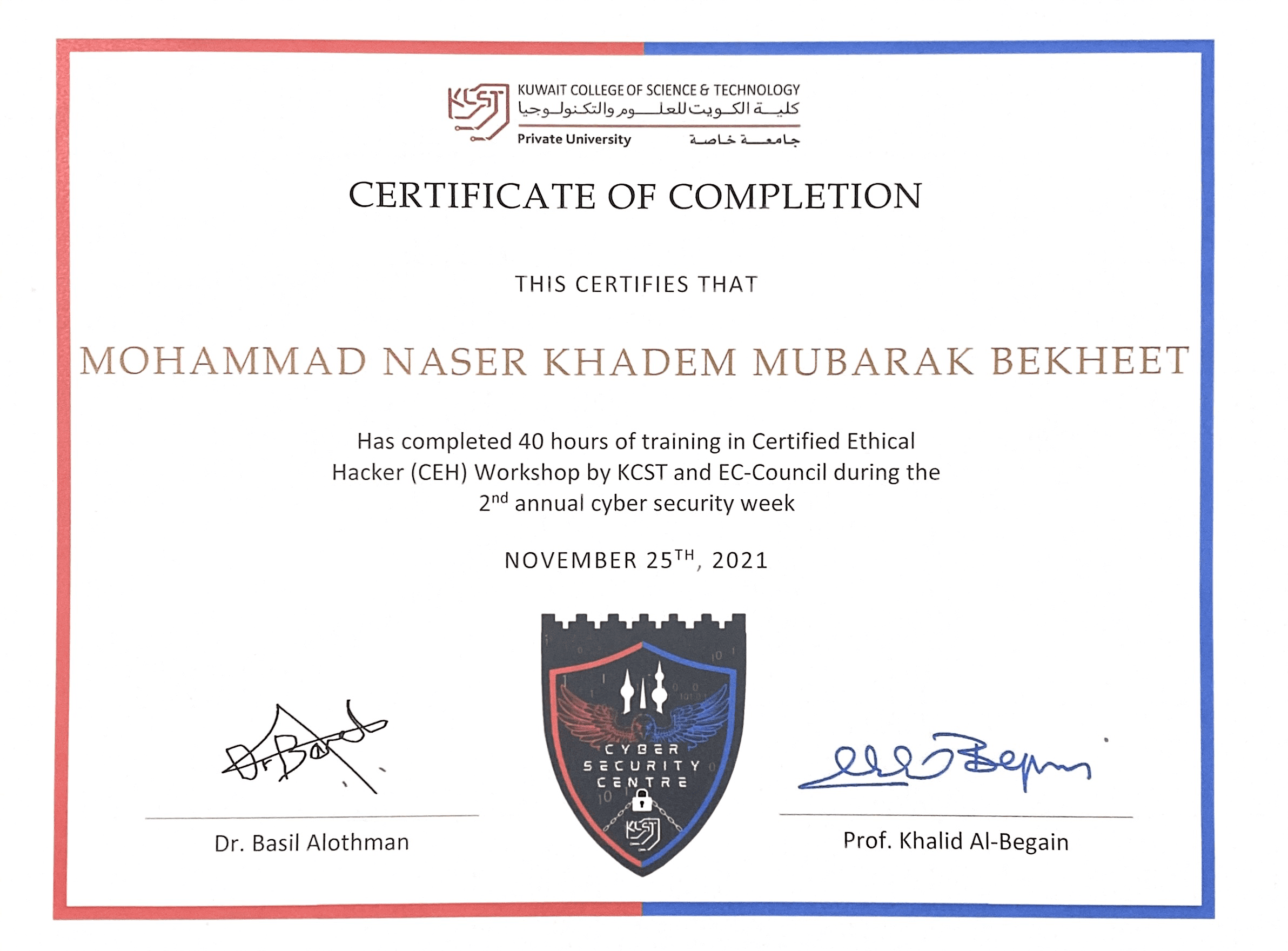
I am proud to hold a certificate for successfully completing a comprehensive
40-hour training program in Certified Ethical Hacking (CEH). This intensive course
provided me with a solid foundation in ethical hacking methodologies, techniques,
and best practices. Through hands-on exercises and real-world simulations, I
gained practical experience in identifying vulnerabilities, conducting penetration
tests, and implementing effective security measures. This immersive training equipped
me with the skills necessary to assess and strengthen the security posture of computer
systems, networks, and applications. Obtaining this certificate demonstrates my
commitment to continuous learning and professional development in the field of
cybersecurity, positioning me as a capable and knowledgeable practitioner in the
ever-evolving landscape of information security.
Date : ( 21 / 11 / 2021)
I am honored to have received a prestigious certificate from EC-Council for successfully
completing the Certified Ethical Hacker (CEH) training. This rigorous
program, recognized worldwide, has equipped me with advanced skills and
knowledge in ethical hacking techniques, methodologies, and defensive strategies.
Throughout the training, I gained a comprehensive understanding of network security,
vulnerability assessment, and penetration testing methodologies. By obtaining this
esteemed certificate, I have demonstrated my commitment to upholding ethical
standards in cybersecurity and my proficiency in identifying and mitigating
potential threats. This recognition from EC-Council further solidifies my
expertise in the field of ethical hacking and strengthens my ability to contribute
effectively to the security landscape.
date : ( 21 / 11 / 2021)
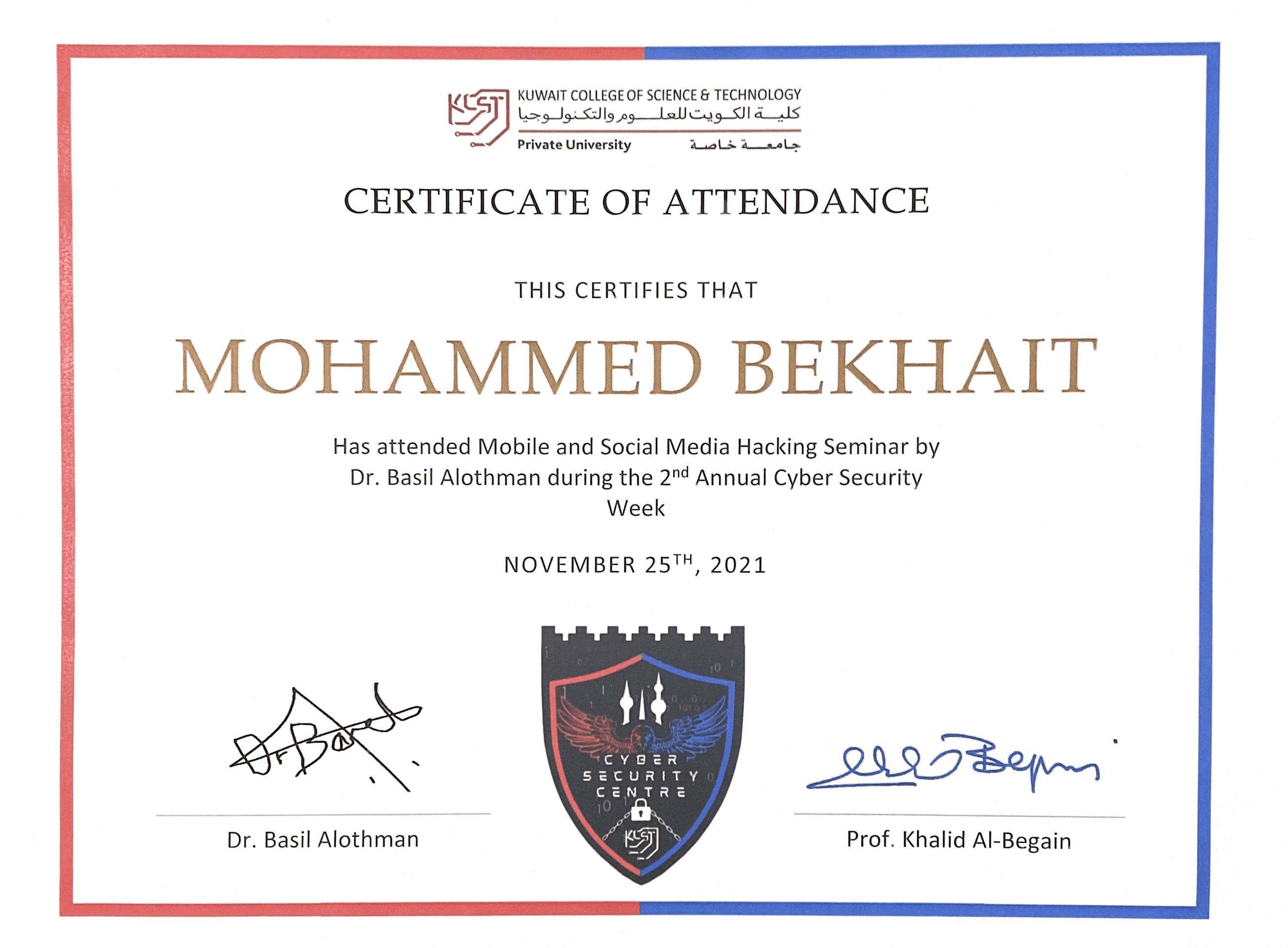
I am delighted to possess a certificate awarded by my university
for actively participating in the Mobile & Social Media Hacking
Seminar during the Annual Cyber Week. This seminar provided valuable
insights into the vulnerabilities and security risks associated with
mobile devices and social media platforms. Through engaging presentations
and hands-on demonstrations, I deepened my understanding of the latest
hacking techniques, threat vectors, and countermeasures in the context
of mobile and social media platforms. Attending this seminar allowed me
to broaden my knowledge and stay abreast of emerging trends in cybersecurity.
This certificate serves as a testament to my dedication to continuous
learning and my commitment to staying ahead in the ever-evolving field of cybersecurity.
date : ( 21 / 11 / 2021)